Exploring Request Interceptors
Understanding Interceptors
Interceptors are essential tools for monitoring and analyzing network communication, allowing cybersecurity professionals to observe how two or more computers interact. By capturing and inspecting network traffic, interceptors help in debugging, security testing, and performance analysis.
Interception primarily happens at two key levels: Application Layer and Network Layer.
Application Layer Interception
At the Application Layer, interception is commonly used to analyze and test HTTP/HTTPS protocols and socket communication. This helps in debugging APIs, security testing, and understanding request/response flows.
Popular tools for application-layer interception include:
- Burp Suite – A powerful tool for web security testing.
- ZAP (Zed Attack Proxy) – An open-source security scanner, widely used for penetration testing.
- MITMproxy – A tool specifically designed for intercepting, modifying, and analyzing HTTP/HTTPS traffic.
Network Layer Interception
At the Network Layer, interception is focused on capturing and analyzing raw network traffic at a lower level. This helps in identifying vulnerabilities, tracking network behavior, and diagnosing issues.
Key tools for network-layer interception include:
- Wireshark – A widely used packet sniffer for deep network traffic analysis.
- tcpdump – A command-line network packet analyzer for capturing and inspecting traffic in real time.
This Saturday’s Exploration
Now, as this Saturday’s exploration plan is to understand how Web Application Interception works and maybe build a small one?
(Well, we have a lot of LLMs 🤖 for help… [just for help XD])
Having used Burp Suite (a tool used for request interception) a few years back, I am familiar with the Proxy server concept.
Interceptors vs. Proxies: What’s the Difference?
A proxy server acts as an intermediary that forwards requests and responses between a client (browser) and a server.
Proxies can serve various purposes, including caching, security, filtering, and anonymity—not just interception.
On the other hand, an interceptor is a specialized proxy that focuses on monitoring and analyzing network traffic.
It captures, logs, and sometimes modifies requests and responses.
Popular interceptor tools like Burp Suite and ZAP are essentially proxies with logging and manipulation capabilities, designed specifically for testing and security analysis.
For a little better explanation of proxies, check this out:
What is a Proxy Server?
Designing an HTTP/HTTPS Interceptor
With this understanding of proxy servers, I tried to quickly design an HTTP/HTTPS interceptor.
By default, this is going to be local, so the endpoint IP will be 127.0.0.1.
Basic Plan
- The HTTP interceptor will listen on port 8080.
- Port 8080 will be configured in Firefox as a proxy server, forwarding all browser requests to the interceptor.
- The HTTP Interceptor should capture requests from the client and cache them.
- The HTTP Interceptor should forward the request and cache the response from the server.
- The intercepted data should be displayed to the user.
By just explaining what I’m trying to build, I kinda created software requirements 😅.
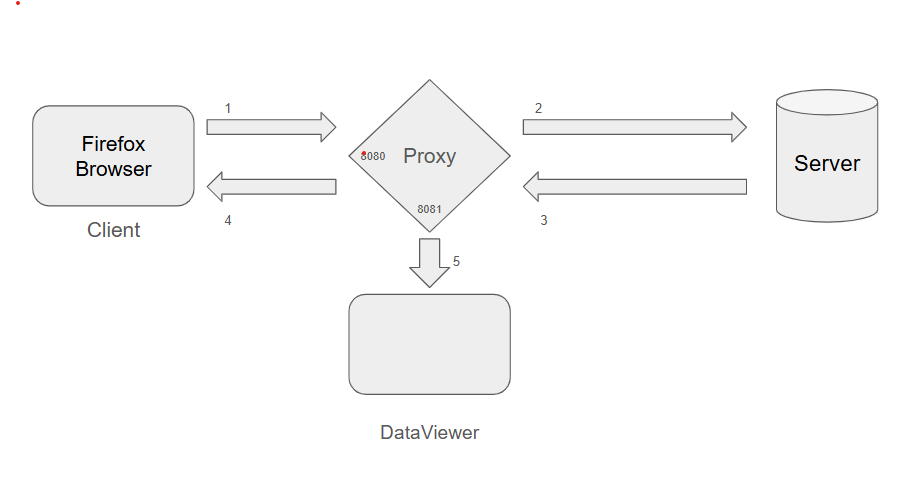
High-Level Design
The above image represents the high-level design and plan for the interceptor.
At this point, I realized I wouldn’t be able to intercept HTTPS requests because that would mean handling TLS/SSL encryption/decryption.
(This will be explored in one of the upcoming Saturdays!)
Building the Interceptor in Golang
I always wanted to explore Golang, so I decided to build this interceptor in Go.
1 | func HandleHTTP(w http.ResponseWriter, r *http.Request, interceptedData *[]map[string]string, mu *sync.Mutex) { |
While running, I came across Firefox’s Captive Portal detection.
A captive portal is used in hotels, cafes, or public Wi-Fi networks to authenticate users before granting internet access.
To read more about it: Firefox Captive Portal.
How the Interceptor Works
- The client (browser) sends a request → received by the proxy server (interceptor).
- The proxy server creates a copy of the request and forwards it to the actual server.
- The server sends a response → the proxy stores it and forwards it back to the client.
Pretty simple! Well… it seemed simple, but it certainly took some time to understand Golang and its libraries.
There were hiccups—like not realizing the server was encoding responses in Gzip. I spent half a day just figuring out what kind of encoding the server was using when sending responses to the client. 🤦♂️
Building the Viewer
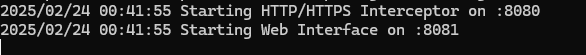
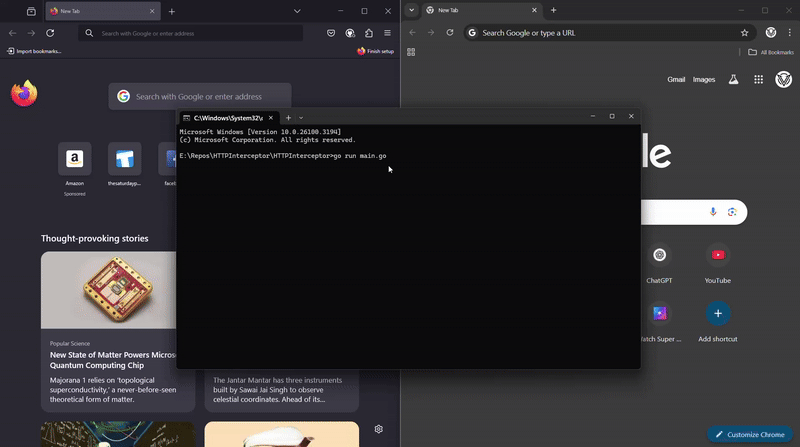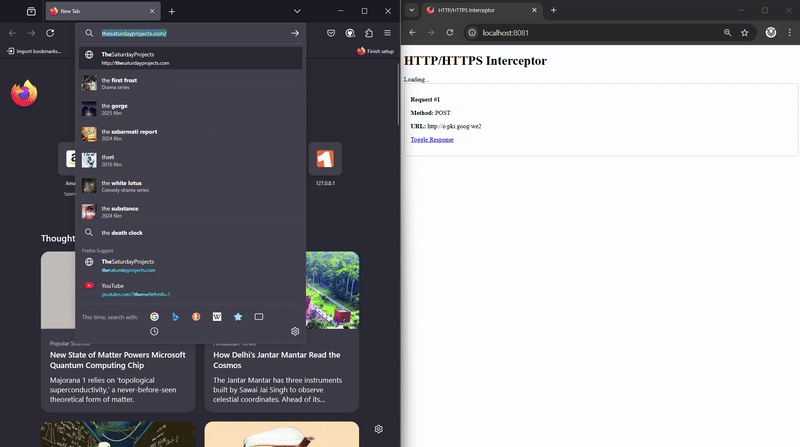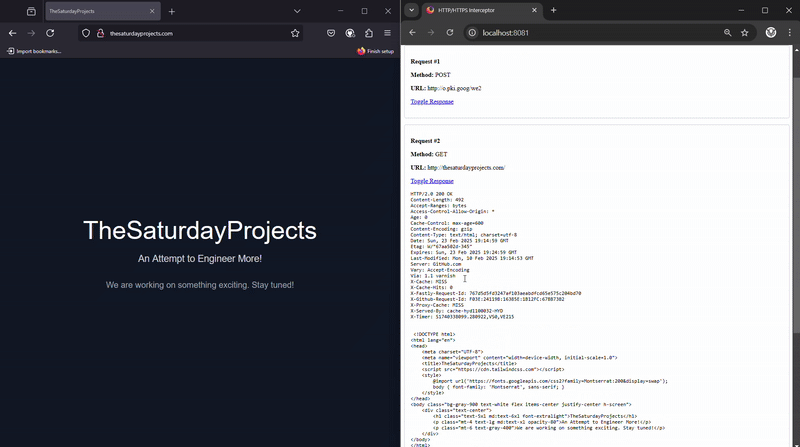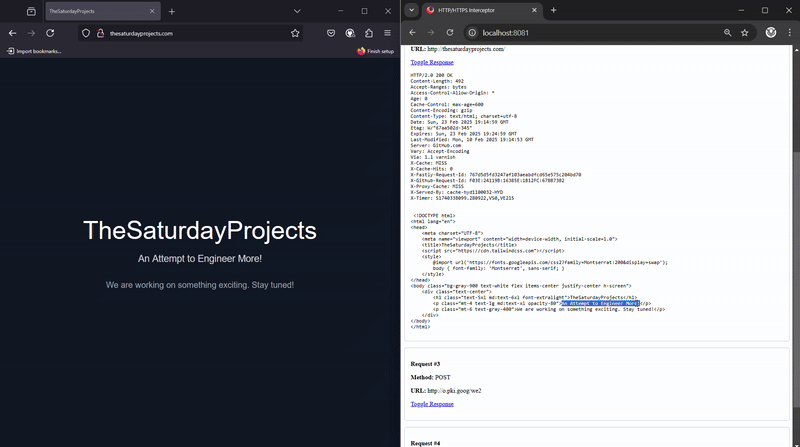
To view the intercepted data, I created a separate HTTP server running on port 8081 within the same Golang app.
This Data Viewer server:
- Uses the intercepted data from the proxy server (8080).
- Serves a vanilla JavaScript UI that requests data every second.
- Displays the intercepted requests and responses dynamically.
Wrapping Up
Though I didn’t cover all the code in this blog, you can find it on my https://github.com/vijayanathan23/HTTPInterceptor.
Thanks for reading from TheSaturdayProjects 🤖!